My server got attacked
Hi, it's Takuya here. I've got good news and bad news for this week. Let's go!
- 📱 Supporting In-App Purchases for iOS 70% done
- 😵💫 Brute force attack on my server
- They exploited the API for the client apps (not the website)
- Implemented a leaky bucket algorithm
- How to prevent similar attacks in the future?
📱 Supporting In-App Purchases for iOS 70% done
I'm currently working on supporting Apple's In-App Purchases for the mobile version of Inkdrop. This week, I implemented a subscription screen and tested it on the iOS simulator (environment=Xcode).
I've also implemented the server-side handling the notifications from App Store. Next week, I'll test it on the sandbox environment and hopefully submit the new build to the App Store.
😵💫 Brute force attack on my server
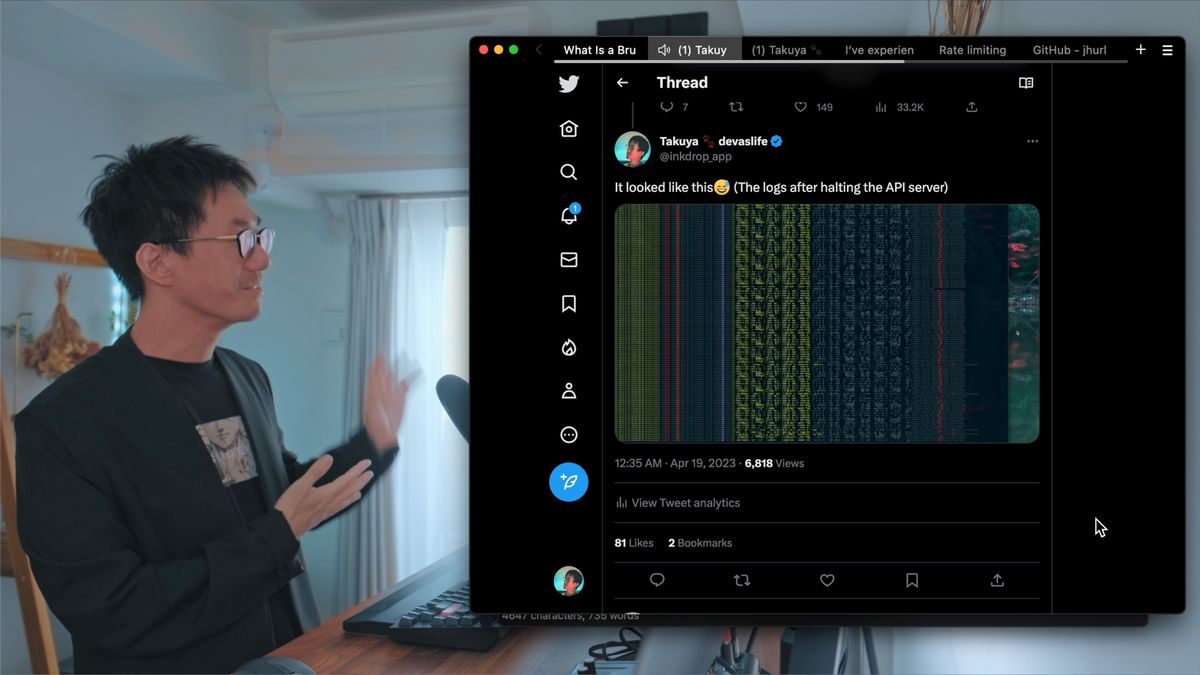
Last Wednesday night, Inkdrop faced an unexpected brute-force attack. Just before going to bed, I received an alert about a high load on the database server. After checking the server logs, I noticed a huge number of requests targeting the API server. A sign-up rush? No, it was rather a brute-force attack on the authentication endpoint using random stolen email addresses and passwords (a.k.a. credential stuffing). The requests came from random IPs, likely from a botnet. It looked like this: